Today I am Going to Explain you that How to Send Trojans as a Text Files that will execute your desired codes..
As you all know that .exe is a Executable File and can run a Code .In this Guide I will teach you How to make a .txt executable that can run all of your codes binded or crypted behind it.
Purpose of Trojan horses?
Trojan horses are designed to allow a hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system it is possible for a hacker to access it remotely and perform various operations. The operations that a hacker can perform are limited by user privileges on the target computer system and the design of the Trojan horse.
Send Trojans as a Text Files
1. First of all You have to download the TEXT ICON PACK. You can download it from internet
2. Extract the Icon Pack to Obtain the Text Icons.
3. Open a new file, Right click - New - Shortcut Type the location of the item:
"X:/WINDOWS\system32\cmd.exe/cfile.txt" (where stands for "X"=Drive)
And name it Readme.txt
4. After creating the readme.txt file right click on it and choose Properties in the Start in fill %currentdir% in the Run choose Minimized
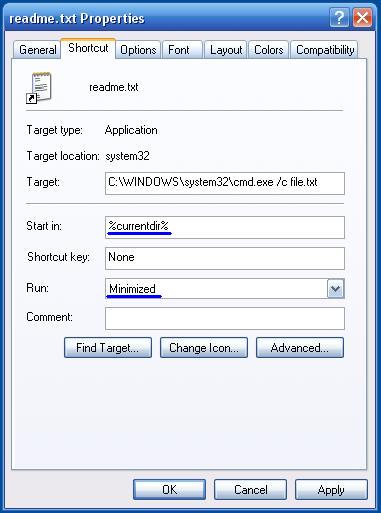
5. Then change the icon with one of the TXT icons from the pack by right clicking the readme.txt file then Properties-Change Icon.
6. In order to execute a file you need one just change your Server/Virus extension to .TXT and name it file.txt Now you have a .TXT Shortcut and .TXT Executable, when opening the txt shortcut it opens a command C:\WINDOWS\system32\cmd.exe /c test.txt" that executes the file you want.
7. Now the readme.txt executes a command window, in order to hide it Right click on the readme.txt and choose properties > Layout and reduced the size on the window to height=1 and width=1. Now change the window position to height=999 and width=999.
8. Now you are ready to sent a trojan as a txt file.
What is RAT or Remote Access Trojan?
Purpose of Trojan horses?
Trojan horses are designed to allow a hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system it is possible for a hacker to access it remotely and perform various operations. The operations that a hacker can perform are limited by user privileges on the target computer system and the design of the Trojan horse.
Send Trojans as a Text Files
1. First of all You have to download the TEXT ICON PACK. You can download it from internet
2. Extract the Icon Pack to Obtain the Text Icons.
3. Open a new file, Right click - New - Shortcut Type the location of the item:
"X:/WINDOWS\system32\cmd.exe/cfile.txt" (where stands for "X"=Drive)

And name it Readme.txt
4. After creating the readme.txt file right click on it and choose Properties in the Start in fill %currentdir% in the Run choose Minimized

5. Then change the icon with one of the TXT icons from the pack by right clicking the readme.txt file then Properties-Change Icon.
6. In order to execute a file you need one just change your Server/Virus extension to .TXT and name it file.txt Now you have a .TXT Shortcut and .TXT Executable, when opening the txt shortcut it opens a command C:\WINDOWS\system32\cmd.exe /c test.txt" that executes the file you want.
7. Now the readme.txt executes a command window, in order to hide it Right click on the readme.txt and choose properties > Layout and reduced the size on the window to height=1 and width=1. Now change the window position to height=999 and width=999.
8. Now you are ready to sent a trojan as a txt file.