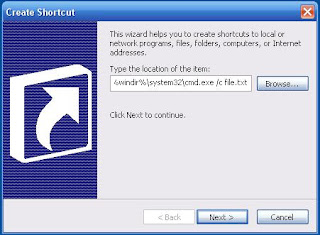
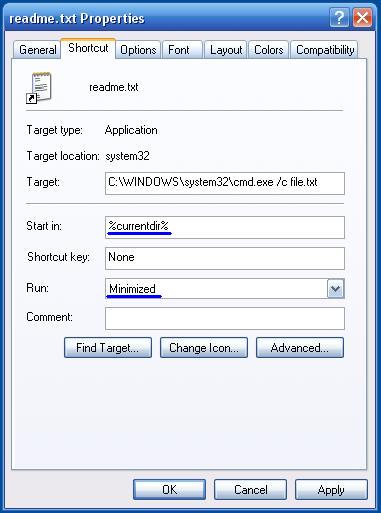
Getting familiar with keyboard shortcuts not only help you get the work done faster, but also more efficient.
Introduction: Keyboard shortcut is a sequence or combination of keystrokes on a computer keyboard which invokes commands in software. Some keyboard shortcuts require the user to press a single key or a sequence of keys one after the other. Other keyboard shortcuts require pressing and holding several keys simultaneously. Keyboard shortcuts may depend on the keyboard layout. Keyboard shortcuts are a common aspect of most modern operating systems and associated software applications. Their use is pervasive enough that some users consider them an essential element of their routine interactions with a computer. Whether used as a matter of personal preference or for adaptive technology
There are various types of Keyboard shortcuts, so I have grouped them up in different Categorizes below:
The General Shortcuts
Dialog Box Keyboard Shortcuts
MMC Console Window Keyboard Shortcuts
Remote Desktop Connection Navigation
Accessibility Keyboard Shortcuts
Microsoft Natural Keyboard Shortcuts
Microsoft Management Console (MMC) Main Window Keyboard Shortcuts
Windows Explorer Keyboard Shortcuts
Shortcut Keys for Character Map
Internet Explorer navigation
Love this article?Share it with your friends on Facebook